-
United States -
United Kingdom -
India -
France -
Deutschland -
Italia -
日本 -
대한민국 -
中国 -
台灣
-
Ansys is committed to setting today's students up for success, by providing free simulation engineering software to students.
-
Ansys is committed to setting today's students up for success, by providing free simulation engineering software to students.
-
Ansys is committed to setting today's students up for success, by providing free simulation engineering software to students.
-
Contact Us -
Careers -
Students and Academic -
For United States and Canada
+1 844.462.6797

Company data, especially when it comes to computer-aided design and engineering (CAD/CAE) simulation files, is one of the most important treasures for an engineering company. Ensuring that this data is kept securely away from hackers and competitors is critical to ensure the health of the company. Recent studies show that the average cost of data breaches has reached a record high of $4.45 million, with a 15% increase over three years. Fifty-one percent of organizations plan to increase security investments because of a breach.
To understand how a critical failure in security could impact a company, it’s important to address securing data early on-premises, on cloud computing, or on hybrid if you use both deployments. The cost of having a secure solution is often much less than the cost of a data breach.

Understanding and Reducing Risk
There are several major concerns listed by customers when it comes to lifting and shifting some of their workloads in the cloud.
First, you must understand that a completely secure place with zero risk does not exist. Some key defense companies or government agencies may decide to disconnect all computers from the network, isolate them in a locked room with ID controls, and protect them in a Faraday cage with encrypted and controlled hardware. If your business is that critical, you may need to look for options beyond the cloud.
For most businesses, however, the question is how to reduce the risk of attacks by investing in security and partnering with organizations that deal with security as their specialty. For example, a cloud solution provided by a top cloud service provider with the highest level of encryption is far more secure than old, easily hackable hardware connected to the internet. To safeguard your business, the initial measure involves gaining a clear understanding of potential attacks. This knowledge enables you to implement preventive measures and thwart any possible threats. Security attacks and countermeasures are constantly evolving, making it difficult for customers to keep up with the latest threats on their own. By using the cloud, your cloud service provider (CSP) will always provide you with the necessary tools to implement security.

Cloud security enables you to work from anywhere.
What Are the Benefits of Using the Cloud for CAE and CAD?
- Security: Cloud storage provides enhanced protection against cyberattacks compared with alternative options. This is attributed to regular backups and off-site storage, which mitigate potential data loss. Cloud storage has countermeasures against cyberattacks, such as restricting access to storage, encrypting data during data transfer, and encrypting data during storage. Additionally, continuous monitoring for suspicious activities adds an extra layer of security. By securely maintaining information off-site in encrypted formats, cloud storage effectively guards against security risks.
- Affordability: You’ll always benefit from the best and latest technologies on your storage. Once it becomes obsolete, it’s replaced by a new generation at no cost, which is impossible to achieve on-premises.
- Recovery of lost files: With data duplication, you can easily recover your projects and files without worrying about backups that are costly and time-consuming. Cloud storage has extremely high availability due to storing data in multiple data centers — for example, the AWS archive storage solution Amazon S3 Glacier has 99.9% data durability. View best practices for Amazon S3 Glacier here.
- File sharing: Your team can work on a single platform where all data is safely controlled. It’s much easier for a sysadmin to control data on a single platform than on multiple hardware devices with no monitoring. It’s also possible to take snapshots to keep copies of important data.
- Accessibility: You can access your data from everywhere and across multiple devices with the level of security that you want to set up, independent of the device. Security policies can be configured using services such as IAM, S3 policies, and others.

Tips for Securing Data on the Cloud
The security of data on Ansys Gateway powered by AWS is a shared responsibility among you (the users), Ansys (the independent software vendor), and AWS (the CSP). The table below illustrates the shared responsibility model for data security for workloads running on AWS using Ansys Gateway powered by AWS.
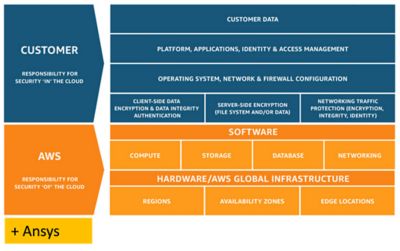
Shared responsibility framework for data security and compliance on AWS
AWS is responsible for providing secure infrastructure, services, and frameworks that are available for users to run their workloads. With the AWS Well-architected Framework, Ansys has made sure to implement the best practices for security, reliability, operational excellence, performance efficiency, cost optimization, and sustainability while architecting and building the product Ansys Gateway powered by AWS. All Amazon EC2 instances available for users come with the AWS Nitro System, which is an advanced hypervisor purpose-built to provide maximum security and performance to users. It is designed using a security chip that monitors, protects, and verifies the instance hardware and firmware.
Along with the above framework, some general recommendations for securing your data while running Ansys workloads are below.
Enable multifactor authentication (MFA): To prevent attacks, the more security you can add for authentication, the better. Ansys provides Ansys ID, a single sign-on solution that enables you to sign in one time and use a single set of credentials to access multiple Ansys products, services, and websites. It helps reduce the number of IDs and passwords so you can keep only one very secure password rather than multiple.
Deactivate old devices: Make sure the old devices you don’t use anymore are removed from the authorized list of devices. This gives you control only on existing and up-to-date devices.
Protect your data: Ansys Gateway powered by AWS secures each Control Plane location with AWS Access Control Lists (ACLs) and web application firewalls (WAFs). All customer data remains generated and stored in the customer’s own AWS environment.
With AWS Identity and Access Management (IAM), customers can define, enforce, and audit user permissions across AWS services, actions, and resources. Customers can use AWS Shield and AWS WAF to protect their data from cyberattacks. Customers can choose to add higher observability features in their AWS account to monitor the data movement and activity using services such as Amazon CloudWatch and CloudWatch Metrics. Data can be further encrypted to higher encryption levels using AWS Key Management Service (KMS). Finally, you can use AWS Budgets and AWS Cost Monitoring services to keep track of your spend and budget for the AWS service consumption.
For more information, please read the white paper “Ansys Gateway powered by AWS — Architecture Overview.”
Read the terms of service: Reading the terms of service helps you understand the level of security deployed into each product to ensure that you are protected. For example, Ansys Gateway powered by AWS will not store any data on a customer’s behalf, so there is no data retention and deletion requirement. Each customer is solely responsible for its data retention and deletion policy and procedure.
Interested in testing our latest Ansys Cloud products? Click here: Cloud-Powered Simulation for Every Engineer.
The Advantage Blog
The Ansys blog, featuring contributions from Ansys and outside experts, keeps you in the know with the latest industry information, including engineering articles and simulation news, thought leadership and trends, product development advances, tips to better use Ansys solutions, and customer stories.